Intro
Some time ago, I received a task to create a report based on Skyhigh SWG (formerly McAfee SWG) configuration. I wanted to automate this task with a Python script that would do all the dirty work for me. To get a script running, I had to feed it with configuration data. I had a choice to get data via API or from a backup file. I chose an API, but after some time, I had to drop the API idea. It turned out to be inefficient for my needs. So the other option left was the backup file.
What is inside
Opening the backup file shows XML structured data with a bunch of info about the device version, timestamp, etc. I found there folowing tags:
- co_generator
- co_timestamp
- co_file
- co_backup_node_list
- co_backup_data
The first one, “co_generator” holds a uuid and a system version of the device that generated the backup. It also holds a timestamp when the backup file was generated, a license type, and the name of the binary that produced the backup.
The second one, “co_timestamp” holds information about a time when the backfile was generated.
The third one, “co_file” shows which configuration snapshot was used to build the backup.
The fourth one, “co_backup_node_list” contains a list with UUIDs of all devices that are connected to the Mangement box.
The fifth one, “co_backup_data” is the most interesting tags from the backup file. It inholds the actual backup from the device.
When I looked at it, my first guess was “that’s base64 encoded”. And I was totally right! So I opened CyberChef, copy/pasted “co_backup_data” content to the input, added “From Base64” and “Detect File Type” to the Recipe and received my output:
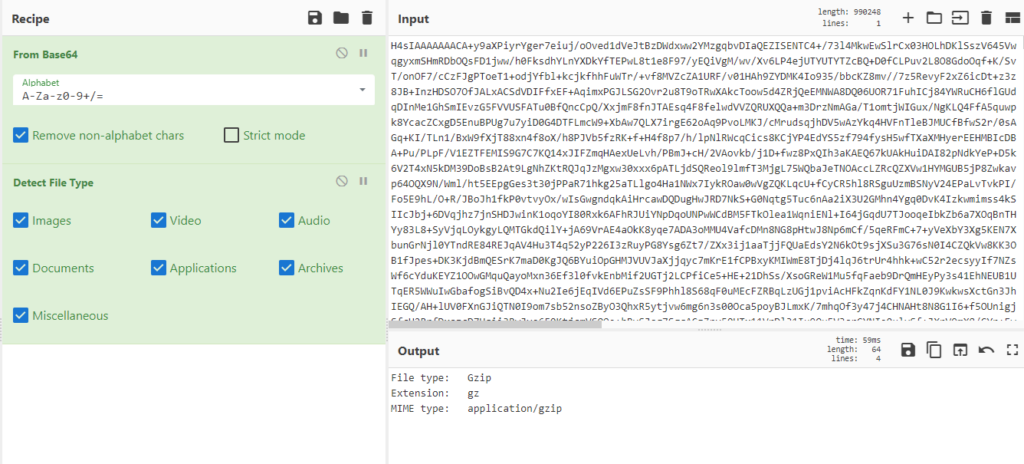
Inside base64 data was a GZip file. So I downloaded it, unzipped it with 7-zip, and found another unknown file type. This time I opened WSL (Windows Subsystem for Linux) and issued a “file” command to check the unzipped file.
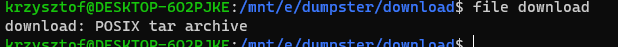
Inside Gzip file there was a tar archive. So “tar -xf download” and I found this:
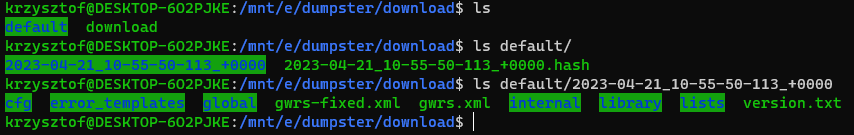
Decoded, unzipped, and extracted SWG configuration. The folder structure is the same as you can find in /opt/mwg/storage on the device itself.
How to easily get it
Getting the configuration files manually from the backup is not the fastest way. You have to open a text editor to pick base64 data from an XML file and decode it with some tool capable of base64 decoding. Then you have to unzip (gunzip, 7-zip) and after untar (tar, 7zip) extracted file. So you must use a few methods to get the data you want.
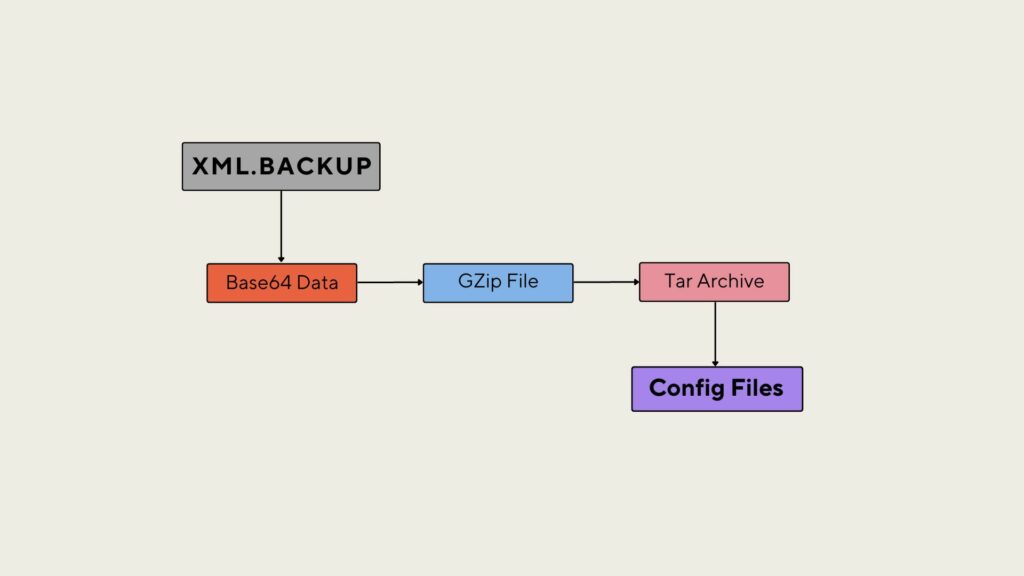
Having the above in mind, I was able to develop a simple Python utility script. It takes the backup file as an argument and extracts it into the current working directory.
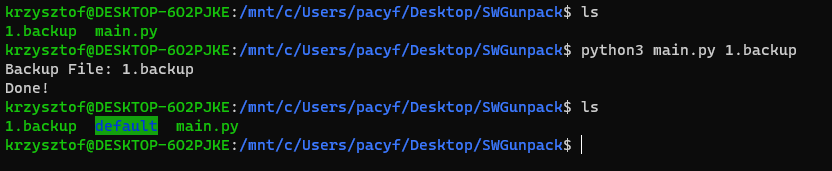
SWGunpack utility can be found on our public GitHub Repository: https://github.com/firewallops/SWGunpack
If you like this post and provided utility, you can find similar articles here.





Leave a Reply